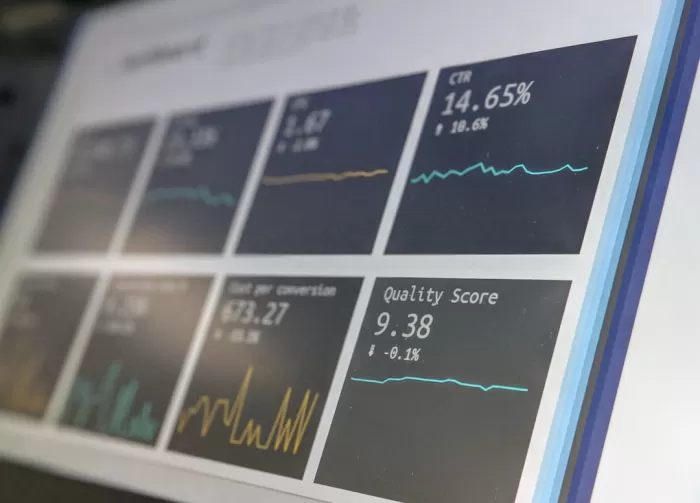
How Hackers Exploited T-Mobile’s Weaknesses: A Deep Dive
An exploration of the events leading to the T-Mobile data breach, including vulnerabilities, hacker tactics, and the aftermath.
Read More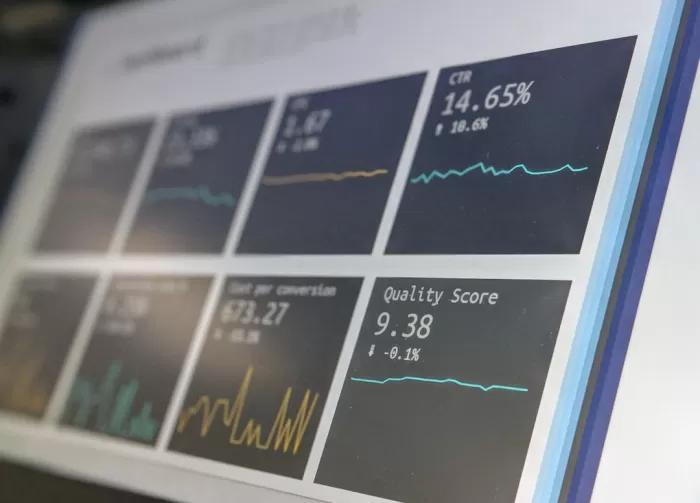
T-Mobile Security Breach: What Happened and Who Was Affected
An overview of the recent security breach at T-Mobile, including its impact and response.
Read More