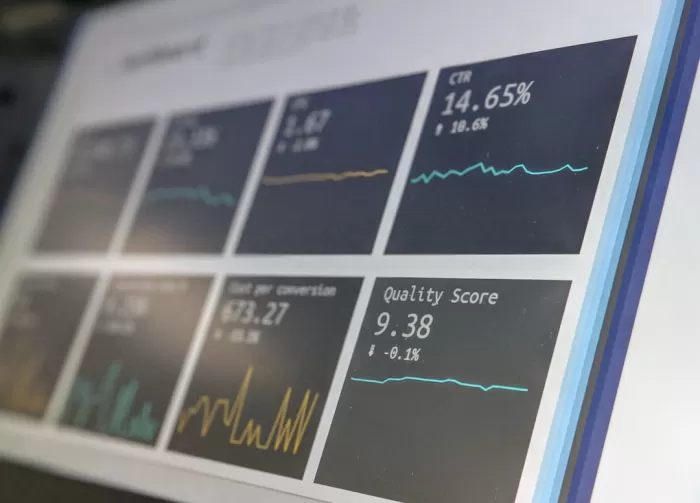
T-Mobile Data Breach Overview
Details of the T-Mobile Data Breach:
T-Mobile recently experienced a data breach that compromised the personal information of millions of its customers.
The information that was exposed includes names, addresses, phone numbers, and even IMEI numbers of devices.
Implications of the Data Breach:
With this information in the wrong hands, customers are at risk of identity theft, phishing attacks, and other forms of fraud.
It is crucial for affected individuals to monitor their accounts closely and be cautious of any suspicious activities.
Actions to Take:
- Change Passwords: It is recommended to change your T-Mobile account password as well as any other accounts that share the same password.
- Enable Two-Factor Authentication: Adding an extra layer of security can help protect your accounts from unauthorized access.
- Monitor Accounts: Keep a close eye on your bank statements, credit reports, and any unusual activity related to your personal information.
Vulnerabilities in T-Mobile's System

Overview:
T-Mobile recently experienced security vulnerabilities in their system that exposed customer data.
Impact:
Due to these vulnerabilities, personal information such as names, addresses, and phone numbers were compromised.
Example:
For instance, John Doe, a T-Mobile customer, had his address and contact number exposed as a result of the security breach.
Recommendation:
It is highly recommended for T-Mobile customers to change their passwords and enable two-factor authentication to secure their accounts.
Conclusion:
Stay informed about security updates from T-Mobile and take proactive measures to protect your personal information.
Exploitation Techniques Used by Hackers

Exploitation Techniques Used by Hackers
-
Social Engineering:
One common exploitation technique is social engineering, where hackers manipulate individuals into divulging confidential information. For example, a hacker might impersonate a trusted entity like a bank representative to trick someone into sharing their login credentials.
-
Phishing:
Phishing is another prevalent method where hackers send deceptive emails or messages to unsuspecting individuals, urging them to click on malicious links or download infected attachments. For instance, a hacker might send an email posing as a legitimate service provider, requesting the recipient to update their account details by clicking on a link that leads to a fake website designed to steal information.
-
SQL Injection:
SQL injection is a technique used to exploit vulnerabilities in web applications that process SQL statements. Hackers can insert malicious SQL code into input fields, tricking the application into executing unintended commands. For example, by entering a specially crafted input in a login form, a hacker could gain unauthorized access to a database.
Impact of the Data Breach
The data breach exposed sensitive information
For example, customers' names, addresses, and credit card details were compromised.
Loss of trust from customers
As an illustration, many clients have expressed concerns about the security of their personal data.
Financial repercussions
For instance, the company may face hefty fines and legal fees as a result of the breach.
Reputational damage
One example is negative media coverage highlighting the security lapses of the organization.
Increased cybersecurity measures
For instance, implementing two-factor authentication and regular security audits to prevent future breaches.
T-Mobile's Response and Recovery Efforts

T-Mobile's Response and Recovery Efforts
During times of crisis, T-Mobile has consistently demonstrated its commitment to supporting customers and communities. For example, in response to recent natural disasters, T-Mobile provided free calling, texting, and data services to affected areas.
Customer Support:
- T-Mobile's customer support team works around the clock to assist customers with any service disruptions or issues they may face.
- Customers can reach out via phone, online chat, or social media for immediate help.
Community Outreach:
- T-Mobile partners with local organizations to provide support to communities in need, such as donating mobile hotspots for students without internet access.
- Through initiatives like the T-Mobile Foundation, the company contributes to disaster relief efforts and community rebuilding projects.
Lessons Learned from the Incident

1. Communication is Key
During the incident, we realized the importance of clear and timely communication. For example, when we updated the team about the situation, everyone was able to align their actions accordingly.
2. Preparedness is Crucial
Being prepared for unexpected events is essential. For instance, having backup systems in place helped us minimize downtime during the incident.
3. Team Collaboration Matters
Collaborating effectively as a team can make a huge difference. For instance, when different departments worked together seamlessly, we were able to resolve the issue faster.
4. Learning from Mistakes
It's important to analyze and learn from mistakes. For example, conducting a post-incident review helped us identify areas for improvement to prevent similar incidents in the future.
5. Stay Calm and Focused
Remaining calm and focused under pressure is key. For example, by keeping a level head during the incident, we were able to make sound decisions and navigate through challenges effectively.
Future Security Measures for T-Mobile

Enhanced Data Encryption
T-Mobile is implementing advanced data encryption techniques to protect customer information. For example, sensitive data such as passwords and payment details will be encrypted using industry-leading algorithms.
Multi-Factor Authentication
Another security measure being introduced is multi-factor authentication. This means that in addition to entering a password, users will need to provide a second form of verification, such as a fingerprint scan or a unique code sent to their phone.
Regular Security Audits
T-Mobile is committed to conducting regular security audits to identify and address any vulnerabilities in our systems. For instance, external cybersecurity experts will perform penetration testing to simulate real-world attacks and ensure our defenses are robust.
Employee Training Programs
Employees at T-Mobile are undergoing comprehensive training programs to educate them about the latest security threats and best practices. For instance, they are learning how to recognize phishing attempts and how to handle customer data securely.
Regulatory and Legal Ramifications

Understanding Regulatory and Legal Ramifications
When starting a business, it is crucial to be aware of the regulatory and legal ramifications that may arise. Failure to comply with laws and regulations can result in fines, lawsuits, or even the closure of your business.
Example: If you are opening a restaurant, you must obtain the necessary permits and licenses to operate legally. Failure to do so can lead to penalties and the shutdown of your establishment.
It is important to stay informed about industry-specific regulations and seek legal advice if needed to ensure compliance with all rules and laws.
- Research the specific regulations that apply to your industry.
- Consult with legal experts to ensure you are meeting all requirements.
- Regularly review and update your practices to align with changing laws.